Advanced Infostealer Malware Detection.
Protect Your _Business
Detect compromised credentials in infostealer malware logs, notify affected employees privately, and empower them to take action — closing the loop on credential theft.
Account Protection
Detect compromised credentials in stealer logs, then notify affected employees privately through Lens — empowering them to change passwords and complete security training.
Malware Detection
When staff devices are infected by infostealer malware, detect it fast. Alert your security team and guide affected users through private remediation with built-in training.
Realtime Data Access
APIs allow fast access to your data, and webhooks allow fast integration into your SOC, ticketing system, or channels.
Powerful Features
Track down IOCs
We instantly flag compromised credentials to proactively identify known Indicators of Compromise (IOCs) in your environment before they can cause damage.
Native STIX 2.1 Export
Export threat intelligence in STIX 2.1 format for direct ingestion into Splunk, Microsoft Sentinel, and other SIEMs.
Designed for MSPs and SOCs
With webhook and templated callbacks into many common ticketing systems, alerts will be pushed to the right people as soon as they're fired.
Cryptographically secure APIs
Our credential check API allows near realtime, anonymous checking of credential pairs against billions of rows of stolen data.
SSO and Advanced Security Login
Login to the service using your own SSO provider, or use more traditional username and passwords with enforced 2FA or Passkeys.
CSV data exports
Data is available to download in convenient formats for immediate ingress into your systems.
Comprehensive Dashboards
See a snapshot of your data, and changes over time.
Data encrypted at rest
We take your data seriously. All data is encrypted at rest and in transit.
Built by Cybersecurity Engineers
We understand the threats you face, and have built a platform that is designed to help you protect your business.
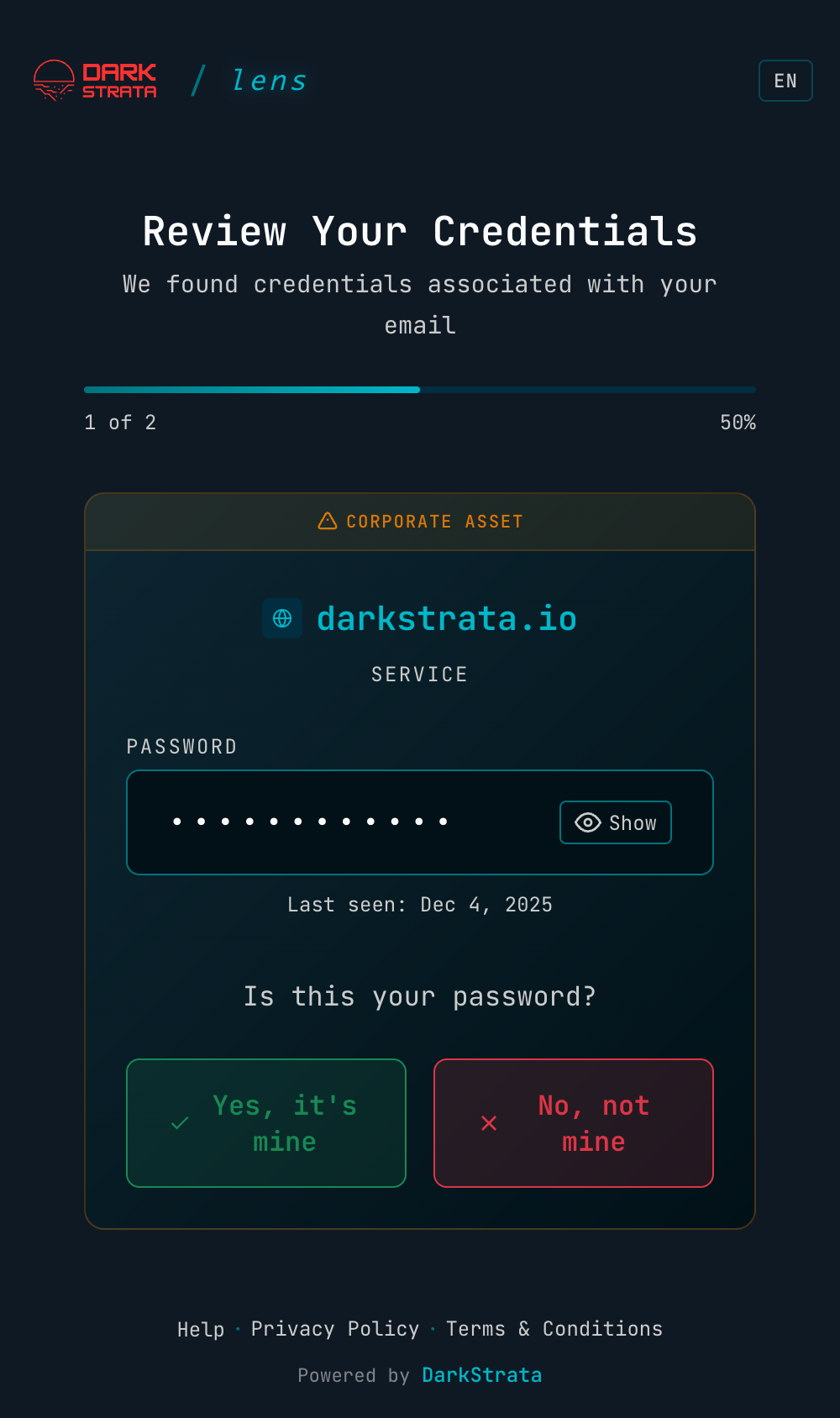
Private Security Awareness for Your Team
When employees are found in stealer logs, notify them privately. Users review their compromised credentials, complete security training, and take action — without admins ever seeing their passwords.
- Privacy-first: admins never see passwords
- Mobile-friendly experience
- Built-in security training
- Track completion, not private data
Simple, Transparent Pricing
Choose the plan that fits your organisation's size and security requirements.
Basic
Essential protection for growing teams
Pro
Advanced features for security teams
Enterprise
Complete solution for large organisations
Built for SOCs, honed for MSPs, perfect for Small Businesses.
The DarkStrata platform was crafted by Cybersecurity-focused Software Engineers with a proven track record in threat intelligence.
- Unlimited domains and sub-domains
- Secure by design
- Simple alerting
- Close the loop with private employee notifications
- Manage your customer's data in n-tiers
- Realtime access via APIs
- Integrate into your own ticketing systems via powerful webhooks
- Native STIX 2.1 export for SIEM integration
- Affordable pricing
Got any Questions?
We're here to help you understand how DarkStrata can protect your organisation.